TCP/IP is a fundamental communication protocol suite that enables all devices connected to the internet to communicate with each other. It stands for Transmission Control Protocol/Internet Protocol and is responsible for ensuring reliable transmission of data between devices. In simple terms, TCP/IP is the backbone of the internet and without it, the world as we know it would not exist.
For many people, the technical aspects of TCP/IP may seem daunting and complex. However, understanding the basics of this protocol suite is essential for anyone working in the field of networking or for those who simply want to have a deeper understanding of how the internet works. In this article, we will explore the various aspects of TCP/IP, its components, and its role in modern networking.
What is TCP/IP?
TCP/IP is a set of protocols that define how computers communicate over a network. It is a collection of rules and procedures that determine how data is transmitted between devices on the internet. TCP/IP is often referred to as the internet protocol suite because it is used by almost all devices connected to the internet.
TCP/IP comprises protocols that specify how computers interact over a network
History of TCP/IP
The origins of TCP/IP can be traced back to the late 1960s when the US Department of Defense started developing a communication protocol for their Advanced Research Projects Agency Network (ARPANET). This was the predecessor of the internet and was developed to link computers at different locations to share resources and information. In 1974, the first version of TCP/IP was developed by Vinton Cerf and Robert Kahn, which became the foundation of modern networking.
Over the years, TCP/IP has evolved and been improved upon to adapt to the changing needs of the internet. Today, it is the primary protocol used for communication between devices on the internet and has become an integral part of our daily lives.
How TCP/IP Works
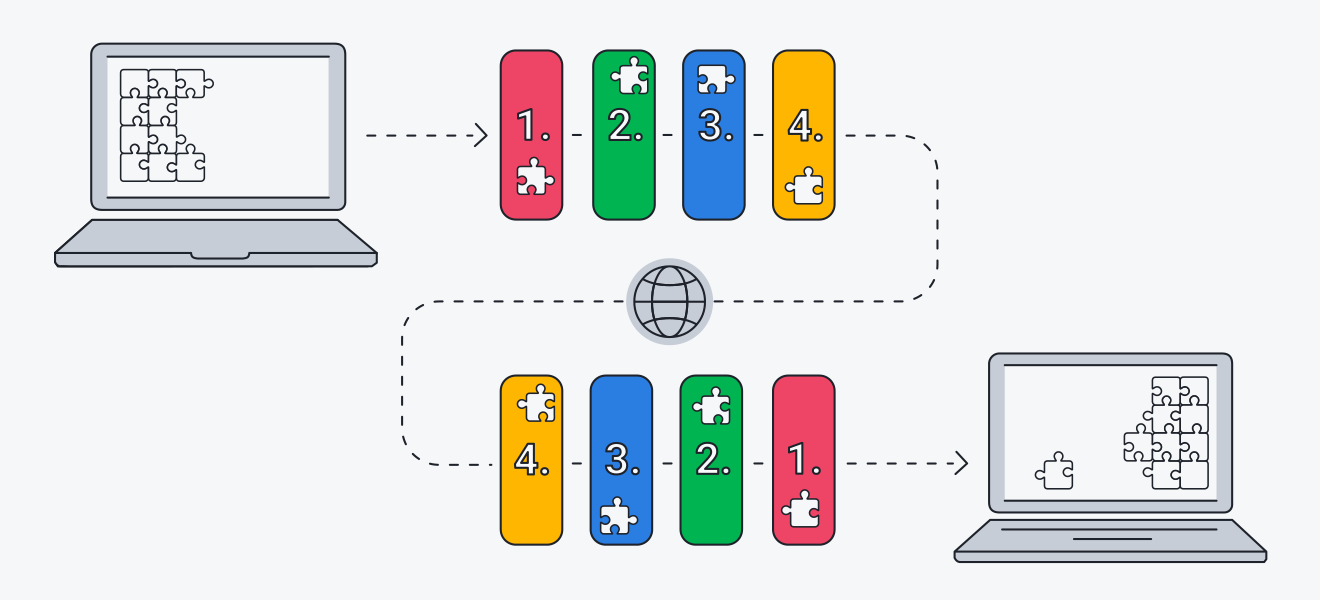
TCP/IP works by breaking down data into small packets and routing them through a network of interconnected devices. It is composed of two main protocols, namely the Transmission Control Protocol (TCP) and the Internet Protocol (IP).
The TCP protocol handles the transfer of data between devices by establishing a reliable connection and ensuring that all packets are delivered in the correct order. On the other hand, the IP protocol is responsible for routing packets through the internet to their final destination.
To understand how these protocols work together, let’s take an example of sending an email from one computer to another. When you hit the send button, the email is broken down into smaller packets and sent over the internet. The TCP protocol ensures that all the packets are received and reassembles them in the correct order on the receiving end. The IP protocol then takes over and routes the packets through the internet to their destination.
Components of TCP/IP
TCP/IP is not a single protocol but rather a suite of protocols that work together to facilitate communication between devices. Here are some of the key components of TCP/IP:

TCP/IP is not a single protocol but a collection of protocols that collaborate to enable communication between devices
Internet Protocol (IP)
As mentioned earlier, the IP protocol is responsible for the routing of packets across the internet. It assigns a unique address to each device connected to the internet, called an IP address, which allows devices to identify and communicate with each other.
There are two versions of the IP protocol, IPv4 and IPv6. IPv4 uses a 32-bit address, while IPv6 uses a 128-bit address. With the increasing number of devices connected to the internet, IPv6 was developed to accommodate a larger number of addresses compared to the limited pool of addresses available in IPv4.
Transmission Control Protocol (TCP)
TCP is responsible for ensuring that data is reliably transmitted between devices. It establishes a connection between the sender and receiver and breaks down data into smaller packets. It also includes mechanisms to detect and retransmit lost packets, which ensures that all data is received in the correct order on the receiving end.
User Datagram Protocol (UDP)
Similar to TCP, UDP is also responsible for sending and receiving packets of data. However, it does not have the same mechanisms for error correction and reliability as TCP. This makes it faster but less reliable than TCP and is often used for applications where speed is more important than accuracy, such as streaming media or online gaming.
Internet Control Message Protocol (ICMP)
ICMP is used to send error messages and diagnostic information when there is a problem with data transmission. It plays a crucial role in maintaining the integrity of the network and helps identify and resolve issues quickly.
How Devices Communicate using TCP/IP
Now that we have covered the basics of TCP/IP, let’s take a closer look at how devices actually communicate using this protocol suite.
Establishing a Connection
The first step in sending data using TCP/IP is establishing a connection between two devices. This is done through a process called a 3-way handshake, which involves three steps:
- The sender sends a SYN packet (synchronization) to the receiver, indicating that it wants to establish a connection.
- The receiver responds with an ACK (acknowledgment) packet, which acknowledges the request and indicates that it is ready to receive data.
- The sender then replies with another ACK packet, completing the handshake and establishing a connection.
Data Transfer
Once a connection has been established, data can be transmitted between the two devices. As mentioned earlier, data is broken down into smaller packets and sent over the internet. Each packet contains the necessary information, such as the IP address of the sender and receiver, the sequence number of the packet, and the data itself.
On the receiving end, the packets are reassembled in the correct order to form the original data. This is done using a sequence number that is attached to each packet, which allows the receiver to reconstruct the data in the correct order.
Closing the Connection
After all the data has been transmitted, the connection is closed using a mechanism called a 4-way handshake:
- The sender sends a FIN (finish) packet, indicating that it has finished transmitting data.
- The receiver responds with an ACK packet, acknowledging the request.
- The receiver then sends its own FIN packet, indicating that it has finished sending data.
- Finally, the sender responds with an ACK packet, completing the 4-way handshake and closing the connection.
The Benefits of TCP/IP
TCP/IP has many benefits and has played a crucial role in the development of modern networking. Here are some of the key advantages of using this protocol suite:

TCP/IP offers numerous advantages and has been instrumental in the advancement of contemporary networking
Widely Adopted
TCP/IP has become the de facto standard for communication on the internet. It is used by billions of devices globally and is compatible with almost all types of operating systems and network devices.
Reliable Data Transfer
One of the main benefits of TCP/IP is its reliability. By establishing a connection between devices and implementing error correction mechanisms, it ensures that data is transmitted accurately and reliably between devices.
Scalability
As mentioned earlier, IPv6 was developed to address the issue of limited IP addresses in IPv4. This allows for a virtually unlimited number of connected devices, making TCP/IP a scalable solution for the ever-growing number of devices connected to the internet.
Flexibility
TCP/IP is a flexible protocol suite that can be used for various types of communication, such as sending emails, browsing the web, or making video calls. Its versatility makes it suitable for a wide range of applications and use cases.
TCP/IP Security
With the rise of cyber threats and attacks, ensuring the security of data transmitted over TCP/IP has become a top priority. Here are some of the key security measures used to protect data using this protocol suite:
Transport Layer Security (TLS)
TLS is a protocol that provides secure communication between devices by encrypting data in transit. It is primarily used for online transactions, such as online shopping or banking, to ensure that sensitive information, such as credit card details, is protected from unauthorized access.
Virtual Private Network (VPN)
A VPN is a technology that allows for a secure connection between two devices over the internet. It creates an encrypted tunnel that hides data from prying eyes, making it an essential tool for remote workers or anyone who wants to protect their online privacy.
Firewalls
Firewalls are essential components of network security and play a crucial role in protecting data transmitted over TCP/IP. They monitor incoming and outgoing traffic and prevent unauthorized access to a network, making them a vital defense against cyber attacks.
The Future of TCP/IP
As technology continues to evolve, so does the world of networking and communication. While TCP/IP has been the backbone of the internet for decades, there is always room for improvement. Here are some of the ways this protocol suite is evolving to meet the changing needs of modern networking:
Internet of Things (IoT)
The IoT is a network of interconnected devices, from smart home appliances to industrial machinery, that communicate with each other over the internet. As the number of IoT devices grows, so does the demand for more efficient and secure protocols. This has led to the development of specialized versions of TCP/IP to cater to the unique requirements of IoT devices.
Software-defined Networking (SDN)
SDN is an emerging networking architecture that separates the control plane from the data plane, giving administrators more control over their networks. This has led to the development of new protocols and technologies that work alongside TCP/IP to make networks more efficient, scalable, and secure.
Challenges Facing TCP/IP
Although TCP/IP has been the go-to protocol suite for decades, it is not without its challenges and limitations. Here are some of the key issues facing this technology:
Security Vulnerabilities
As mentioned earlier, securing data transmitted over TCP/IP is an ongoing challenge. Cybercriminals are always looking for ways to exploit vulnerabilities in this protocol suite, making it essential for network administrators to stay updated and implement robust security measures.
IPv4 Exhaustion
With the increasing number of connected devices, the pool of IPv4 addresses is fast running out. While IPv6 was developed to address this issue, many networks still rely on IPv4, making it a significant challenge to migrate to the newer version.
Network Congestion
As the demand for bandwidth continues to increase, network congestion is becoming a major concern for organizations. With the rise of data-intensive applications like streaming and gaming, network administrators need to find ways to optimize traffic flow and prevent bottlenecks.
Conclusion
In conclusion, TCP/IP is a fundamental protocol suite that has played a crucial role in shaping modern networking. From its humble beginnings as a communication protocol for the US military to becoming the backbone of the internet, TCP/IP has come a long way and continues to evolve with the changing needs of the digital world.
Understanding how TCP/IP works and its various components is essential for anyone working in the field of networking or those who simply want to have a deeper understanding of how the internet works. With the continuous growth of the internet and the emergence of newer technologies, it is safe to say that TCP/IP will continue to play a vital role in connecting the world and shaping the future of communication.



